Transform your enterprise
with next-generation
technology
- Passwordless Experience
- Privileged Access Management
81% of data breaches happen due to poor passwords. – Verizon Data Breach Investigations Report
The technology world today prefers being passwordless than bear the nuances of managing multiple security keys to access systems. A passwordless authentication works across an integrated ecosystem of applications on-premise, cloud, online, and offline providing a unified user experience and an unprecedented level of identity assurance.
74% of security breaches involve compromised privileged credentials. – Forbes
Privileged Access Management (PAM) allows super-user access to privileged users to fully control critical computer systems, applications, and servers anywhere at any time.
PAM solutions separate privileged accounts, i.e. system administration accounts, from an existing Active Directory and stores them in a secure repository to reduce the risk of those credentials from being stolen. By creating a central repository of privileged credentials, PAM systems provide the highest level of cybersecurity for these credentials, control who is accessing them, track all-access, and monitor for any suspicious activity.
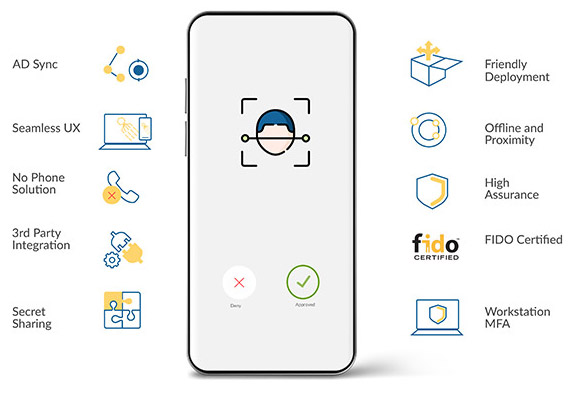
Features of Passwordless Authentication
Weak passwords are the favoured breakthrough point for attackers. Replace password authentication with a secure multi-factor authentication solution to address phishing, credential stuffing, password spraying, mimikatz, and rainbow table challenges.

Password Elimination
01
Enhance security by replacing passwords with a user-friendly and
secure solution that provides a simple touch-and-go login experience
to access workstations, network, and applications.
Passwordless MFA
02
Allow users to access workstation, network, and applications with a unified multi-factor authentication by entering more than one identity proof without the need to remember a password.
Single Sign-on
03
Enable users across your organisation to access all enterprise applications with a completely passwordless single sign-on mechanism.
On Premise or Cloud Deployment
From workstations to servers and applications, one Passwordless Authenticator to rule them all.
On Premise or Cloud Deployment
Utilizing Secret sharing and end to end encryption and mobile enclave to provide the highest level of identity assurance.
Passwordless Login Experience
Provide a single Sign on Solution that covers on premise and cloud applications.
FiDO Certified
Compatible with FIDO2, U2F and UAF.
Stateless Scalable Architecture
Keep identities safe at your on-premise IDP while providing access to cloud applications.

Our Secret Double Octopus Offerings:
Passwordless Authentication
Single Sign-On (SSO)
Password Automation
Multi-Factor Authentication (MFA)
Solution Benefits:
Offers unified authentication to all enterprise applications – legacy and cloud
Eliminates vulnerable passwords
Cost-effective
Prevents phishing, cracking,
and pass-the-hash
Resilient to cyber attacks
Lowers total cost of ownership
Easy integration and
maintenance
Relieves IT workforce from mundane tasks
Pansoft Technologies is your trusted IT Solutions Provider
Pansoft’s Offerings

On-site and Offshore Model

On-demand Support

Dedicated Support

On-premise/Cloud Services

Solution/Process Consulting

Testing

Upgrade

Implementation

About Secret Double Octopus
Secret Double Octopus delights end-users and security teams by replacing passwords across the enterprise with the simplicity and security of strong passwordless authentication. Secret Double Octopus’ easy and seamless experience means users never need to create, change or remember another password to gain high assurance access to domains, networks, cloud and legacy applications.
