Out do the Attackers
with PAM
- Privileged Access Management
- Passwordless Experience
74% of security breaches involve compromised privileged credentials. – Forbes
Privileged Access Management (PAM) allows super-user access to privileged users to fully control critical computer systems, applications, and servers anywhere at any time.
PAM solutions separate privileged accounts, i.e. system administration accounts, from an existing Active Directory and stores them in a secure repository to reduce the risk of those credentials from being stolen. By creating a central repository of privileged credentials, PAM systems provide the highest level of cybersecurity for these credentials, control who is accessing them, track all-access, and monitor for any suspicious activity.
81% of data breaches happen due to poor passwords. – Verizon Data Breach Investigations Report
The technology world today prefers being passwordless than bear the nuances of managing multiple security keys to access systems. A passwordless authentication works across an integrated ecosystem of applications on-premise, cloud, online, and offline providing a unified user experience and an unprecedented level of identity assurance.
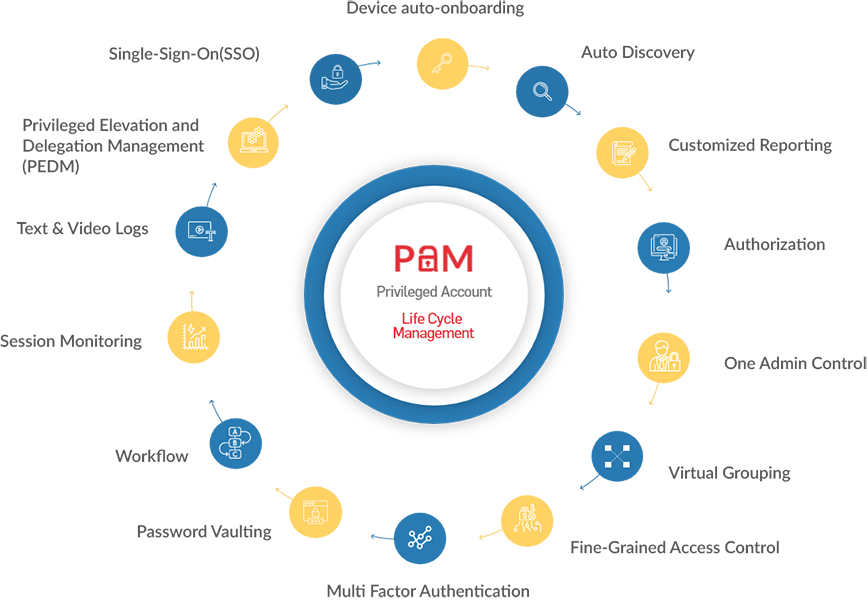
Features of PAM
Since cyber attackers are often times looking for vulnerable passwords and credentials to gain unauthorised access into critical data, PAM is growing to be important for companies having large, complex IT systems.
Our PAM tools and systems are delivered with the following features.


PASM Privileged Account & Session Management
Often referred to as password vaulting, PASM solutions enables privileged users to access specific servers with temporary accounts created for a single session after the vault grants them access. These sessions are recorded and monitored for suspicious activities.

PEDM Privilege Elevation & Delegation Management
A role-based access control solution, PEDM provides access privilege based on job roles. The PEDM tools define which users have access to which part of the system and what can they do with the access granted to them.

Securing Privileged Remote Access
PAM solutions can provide secure remote access for privileged users to access critical internal systems via multi-factor authentication and seamless provisioning and deployment without the need of VPNs.
Auditing File & System Changes
PAM solutions simplify audit by providing detailed audit logs and video recordings for each session for all users. This allows system administrators to prevent unauthorised access and damage to critical resources.
Pansoft Technologies is your trusted IT Solutions Provider

Our PAM Offerings:
Password Vault
Granular Access Control
S.M.A.R.T. Audit Trails
Virtual Grouping
Session Recording
AD Bridging
Solution Benefits:
Secure and manage all access from a central location
Achieve regulatory compliance
Optimise security
Monitor, audit, and control access privileges
Reduce exposure to risks
Prevent internal and external attacks
Pansoft’s Offerings

On-site and Offshore Model

On-demand Support

Dedicated Support

On-premise/Cloud Services

Solution/Process Consulting

Testing

Upgrade

Implementation

Pansoft Technologies has partnered with Arcon, a leading information technology company
specialized in risk control solutions, to provide top-of-the-range risk management services.
Arcon offers a proprietary unified governance framework, which addresses risks across various technology platforms. In the last decade, Arcon has been at the forefront of innovations in risk control solutions, with its roots strongly entranced in identifying business risk across industries. It is in a unique position to react with innovative solutions and products.
